Attribute Based Access Control
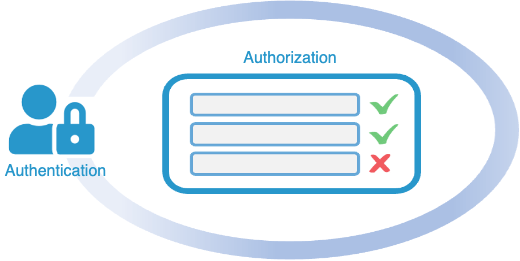
An organization’s applications provide access to protected data, such as financial records, intellectual property, health records, and other sensitive information. Each application, or set of applications, must therefore enforce which users can access which resources.
However, as well as being difficult to manage, the legacy approach of embedding entitlement within applications has major security implications. After authenticating a user, there is a reliance on course-grained access control, which leaves resources vulnerable to unauthorized access and data breaches.
Security vulnerabilities include…
Solution: ViewDS Access Sentinel
Access Sentinel is an authorization server that centralizes access control and strengthens security.
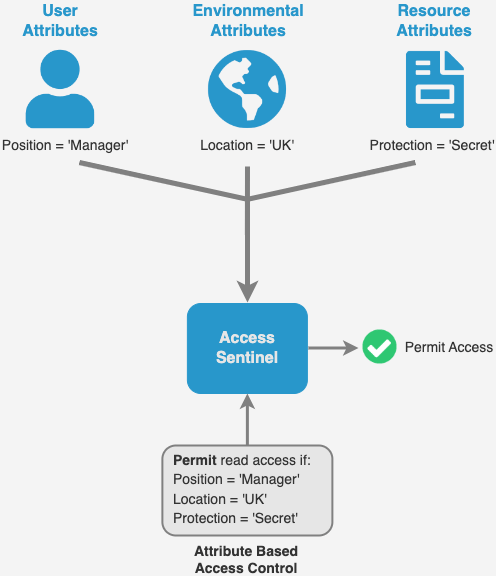
It provides a mechanism to impose policy-based authorization. The natural language of an organization’s security policy, describing who should have access to what and when, is defined in rules using the next level of access control, Attribute Based Access Control (ABAC).
ABAC goes beyond simply defining who has access to which resources by also considering the why, when and where of entitlement.
It controls access to resources according to various attributes or conditions, such as user roles, resource attributes, time of access, location, and more. Entitlement becomes a more precise and tailored mechanism, delivering a high level of security and flexibility.
This deeper level of fine-grained authorization:
ABAC Mitigates Vulnerabilities
The fine-grained authorization provided by Access Sentinel overcomes many potential security vulnerabilities.
Access Sentinel’s XACML Framework
Access Sentinel uses a standardized framework – eXtensible Access Control Markup Language, or simply XACML – to deliver ABAC. The framework provides an architecture, processing model and markup language, that extends access control to include attributes and resource metadata, such as a user’s identity data, their environment, and actions.
- 1
Policy Enforcement Point (PEP), a lightweight component external to each application, intercepts a user’s attempted access.
- 2
PEP asks the Policy Decision Point (PDP) to make an authorization decision.
- 3
PDP assesses the attribute-based access controls (stored as XACML in the PAP), which may also involve considering identity data (in the PIP) such as the user’s security level, job title, or location.
- 4
PDP makes its decision and tells the PEP to permit or deny access.
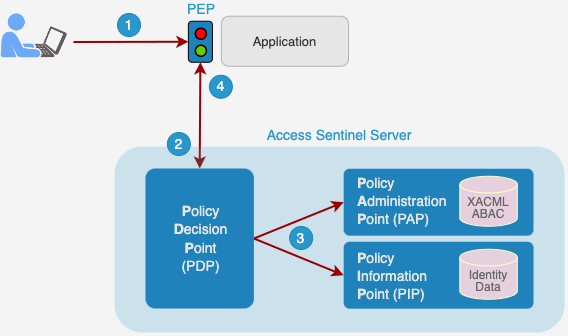
A unique feature of Access Sentinel is that the PDP, PAP and PIP constitute a single component. Consequently, as the XACML policy and identity data reside in a single repository, an admin user can manage the access controls and identity data from a single user interface.



