Zero Trust
The traditional ‘castle and moat’ approach to security establishes a perimeter around the organization’s network and trusts all devices and users within it. However, this approach is highly susceptible to attacks from within the network.
Rather than protecting the perimeter, the zero trust approach is to ‘never trust, always verify’.

ViewDS Access Sentinel
With policy definition and enforcement at its core, ViewDS Access Sentinel delivers critical components of a zero trust architecture.
These are in addition to several other capabilities that either fulfil or support zero trust.
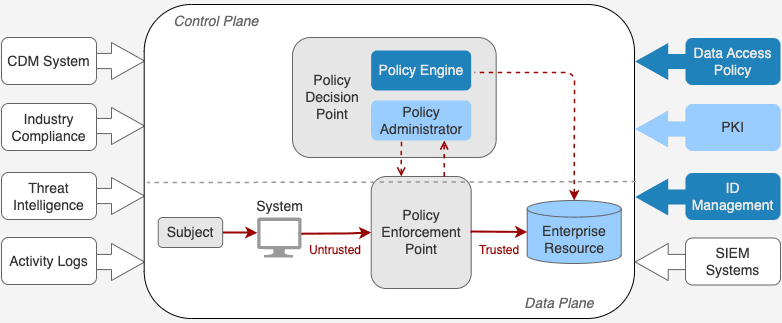
This illustration shows NIST’s zero trust architecture with Access Sentinel’s capabilities in dark blue (full capability) and light blue (supporting capability).
Each capability is described below.